Blog
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
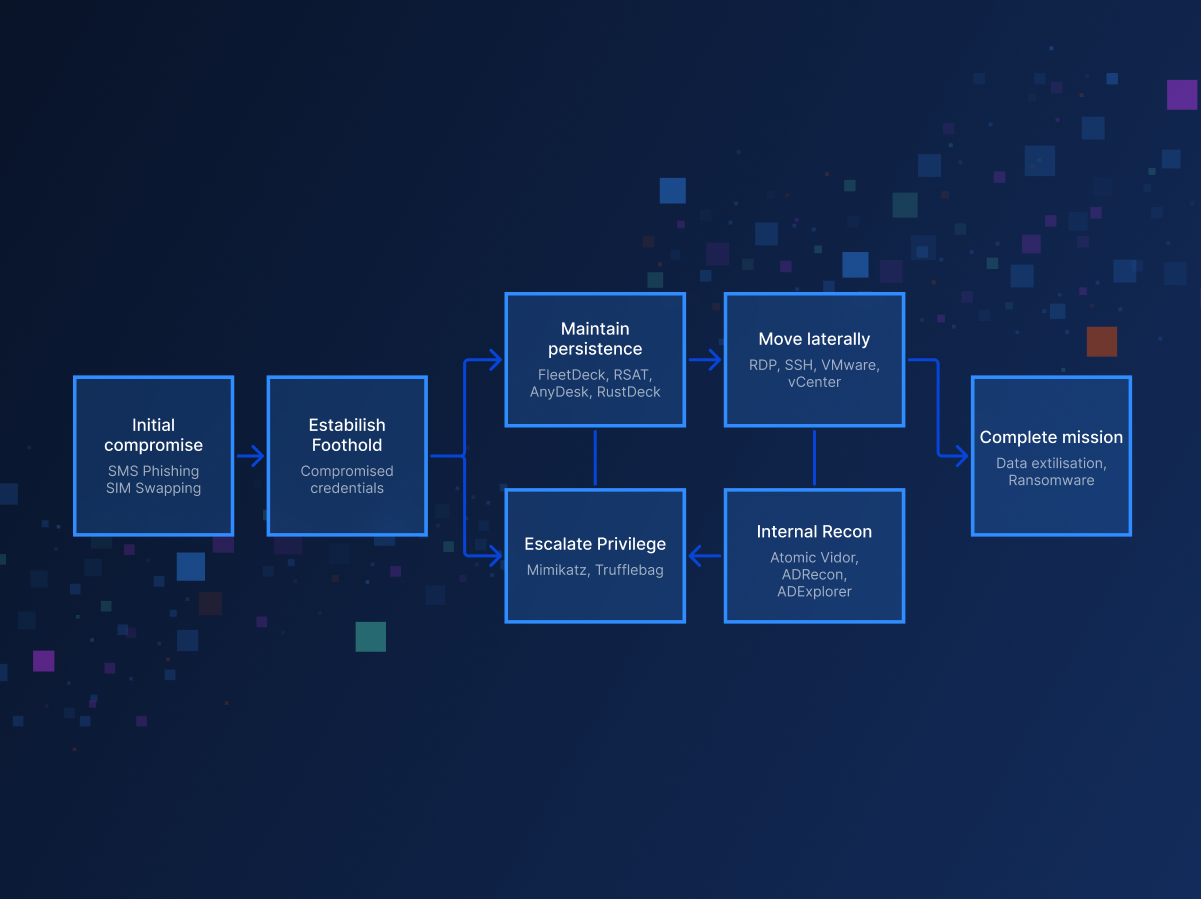
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.

Compliance
/ 14 Sep, 2022The Security and Regulatory Compliance Benefits of WebAuthn
The WebAuthn standard helps you stop phishing and account takeover (ATO) attacks while maintaining HIPAA and SCA compliance.
WebAuthn is significantly safer than passwords, due to the way the keys are stored and because it prevents credential stuffing and reuse attacks.

Security
/ 12 Sep, 2022Phishing Attacks – WebAuthn to the rescue
Authentication token theft is on the rise, with the latest Uber breach demonstrating yet again the threat that it poses.
WebAuthn significantly reduces user experience friction and hence allows for more frequent authentication prompts, offsetting the need for long-lived tokens and significantly curbing the risk of phishing.


