Introduction
Scattered Spider is a highly adaptive, human-operated cybercrime group known for breaching enterprises not only through malware exploits, but by abusing identity, trust, and legitimate access paths. Active since at least 2022, the group is loosely organized, English-speaking, and heavily reliant on social engineering rather than technical zero-days. Their operations frequently involve convincing employees, contractors, or helpdesk staff to reset credentials, enroll new MFA methods, or grant access, allowing the attackers to simply log in as valid users.
What sets Scattered Spider apart is their deep understanding of enterprise identity environments. They target cloud identity providers, SSO platforms, VPNs, and privileged access workflows, often chaining together helpdesk abuse, MFA fatigue, SIM swapping, and token theft to move laterally across identity planes. Once inside, they escalate privileges, disable security controls, and pivot into SaaS, IaaS, and on-prem environments using legitimate tools and sessions. Because their activity closely resembles normal user behavior, traditional perimeter security, endpoint protection, and even MFA often fail to detect them in time.
In short, Scattered Spider don’t hack – they Log In.
They exploit how modern organizations manage identity, trust users, and automate access. This makes them one of the clearest examples of why identity has become the primary attack surface in modern enterprises.
Attack Flow
Scattered Spider operations typically follow a repeatable, identity-centric attack flow rather than a traditional exploit-driven kill chain.
Each phase builds on legitimate access, trusted identity workflows, and normal administrative behavior—allowing the attacker to progress from initial compromise to full mission completion without triggering conventional security controls.
Understanding this flow is critical, because visibility gaps at any phase enable the intrusion to quietly advance across cloud, SaaS, and hybrid identity environments.
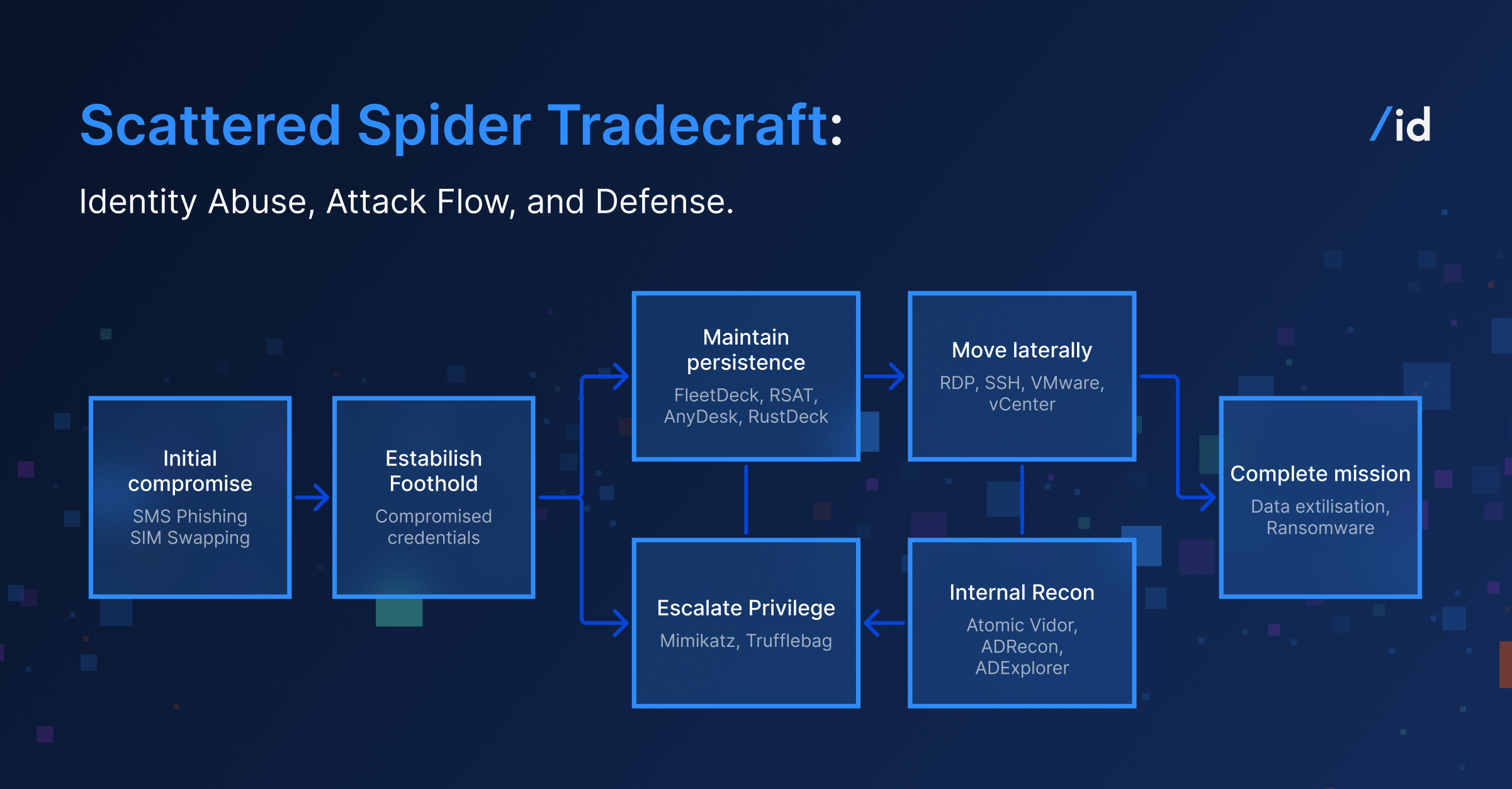
Scattered Spider TTPs
Initial Compromise
Techniques used to gain first access without exploiting software vulnerabilities:
- SMS and voice phishing – vishing (T1598.004) targeting employees and contractors
- Helpdesk impersonation (T1656)
- MFA fatigue (T1621)
- SIM swapping (T1451)
Establish Foothold
- Compromised credentials
- VPN or SSO access using legitimate accounts (TA0007)
- Abuse of conditional access exceptions or legacy authentication paths
Maintain Persistence
Techniques used to retain access even if credentials are rotated (T1219):
- Remote access legitimate software such as Ngrok (S0508), TeamViewer, AnyDesk, RustDesk, FleetDeck, Level.io, Teleport.sh
- Malware such as AveMaria (S0670), RattyRat
- Create accessible VMs (T1578.002) using Tailscale, then dump the AD database ntds.dit on these systems
Escalate Privilege
- Enumeration of roles, groups, and delegated permissions
- Malware such as Mimikatz (S0002), RacoonStealer (S1148)
Internal Reconnaissance
- Enumeration of users, groups, devices, and service principals (T1213.003)
- Conduct AD reconnaissance on on-premises systems using:
- Malware such as Atomic, Vidar, UltraKnot
- Legitimate software such as ADRecon, ADExplorer, PINGCASTLE
Move Laterally
- Delegated admin access misuse across tenants or services
- Use of legitimate remote management and administrative tools such as RDP, SSH, VMware vCenter, Socat Linux Utility
Complete Mission
- Data exfiltration from cloud storage, email, and SaaS platforms
- Ransomware deployment
- Rapid cleanup or abandonment once objectives are met
Mapping to MITRE ATT&CK
| Technique ID | Description |
|---|---|
| T1598.004 | Phishing for Information: Spearphishing Voice |
| T1656 | Impersonation |
| T1219 | Remote Access Tools |
| T1578.002 | Modify Cloud Compute Infrastructure: Create Cloud Instance |
| T1213.003 | Data from Information Repositories: Code Repositories |
Domains Used by Scattered Spider
Scattered Spider uses look-alike domains such as targetsname-sso[.]com or targetsname-helpdesk[.]com to exploit employee trust in familiar identity and IT workflows. These domains are designed to appear legitimate to both users and helpdesk staff, increasing the success rate of credential harvesting, MFA fatigue, and social-engineering calls.
By mimicking SSO, Okta, or service desk infrastructure, attackers can collect valid credentials and session material without deploying malware. This tactic also helps their activity blend into normal identity traffic, delaying detection by traditional security controls.
| Example Domains |
|---|
| targetsname-sso[.]com |
| targetsname-servicedesk[.]com |
| targetsname-okta[.]com |
| targetsname-cms[.]com |
| targetsname-helpdesk[.]com |
| oktalogin-targetcompany[.]com |
Real-World Scattered Spider Campaigns
Caesars Entertainment and MGM Resort Attack
The September 2023 cyber incidents affecting MGM Resorts International and Caesars Entertainment serve as a cautionary example of how identity-centric attacks can disrupt large enterprises without exploiting software vulnerabilities.
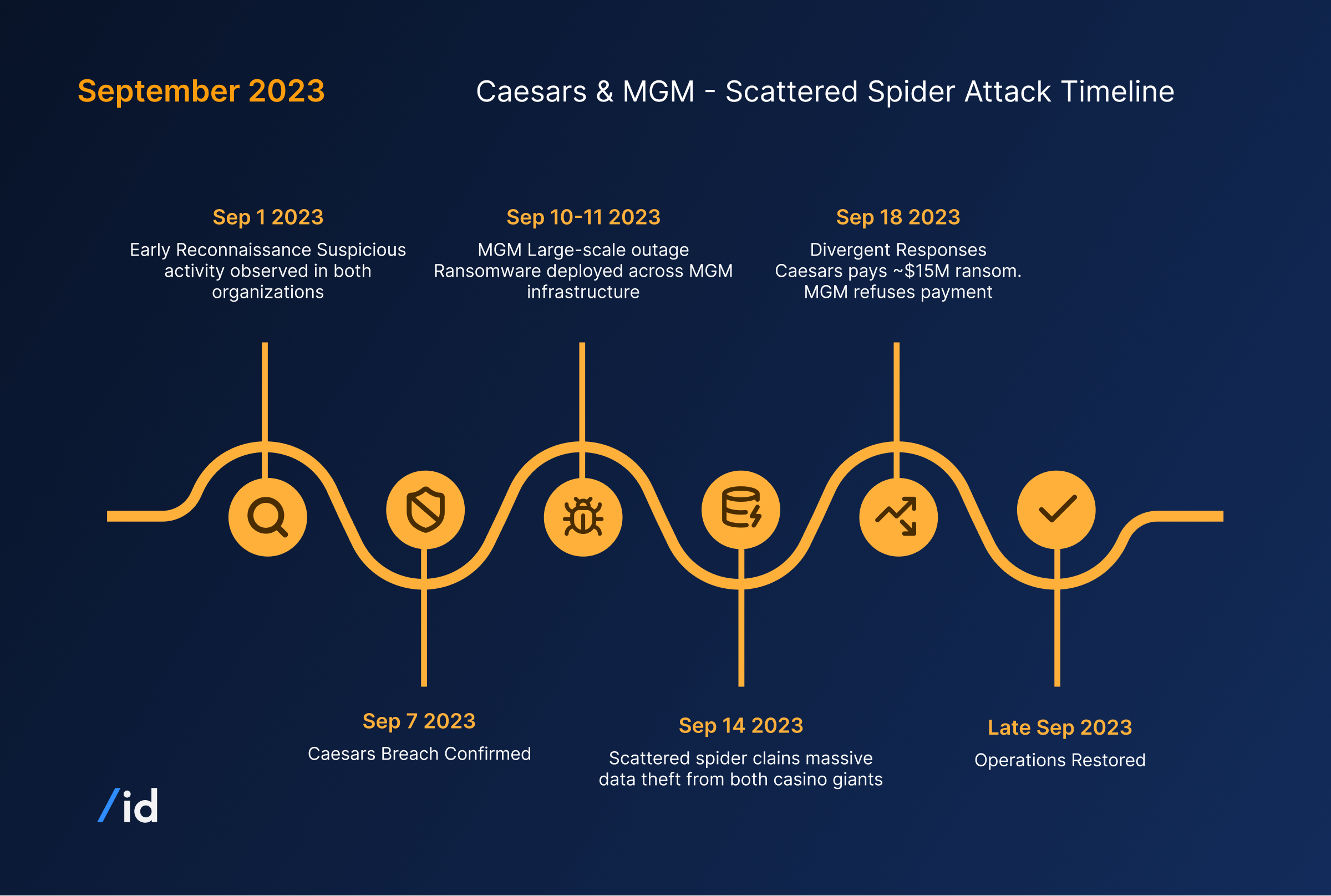
Attack Timeline
| Date | Event |
|---|---|
| Sep 1, 2023 | Early reconnaissance suspicious activity observed in both organizations |
| Sep 7, 2023 | Caesars breach confirmed |
| Sep 10-11, 2023 | MGM large-scale outage; ransomware deployed across MGM infrastructure |
| Sep 14, 2023 | Scattered Spider claims massive data theft from both casino giants |
| Sep 18, 2023 | Divergent responses: Caesars pays ~$15M ransom, MGM refuses payment |
| Late Sep 2023 | Operations restored |
Attack Lifecycle
In both incidents, the attack followed a similar identity-driven lifecycle. Initial access was achieved through social engineering, with attackers impersonating employees to manipulate IT support workflows. This enabled access to identity infrastructure, including Okta, which played a central role in authentication and access management.
Once authenticated as legitimate users, the attackers leveraged weak or inconsistently enforced MFA controls to escalate privileges and expand access across cloud and SaaS environments. Rather than relying on malware exploits, the attackers operated through trusted identity sessions, allowing them to move laterally, access sensitive systems, and exfiltrate data while blending into normal administrative activity.
In MGM’s case, this access ultimately enabled deployment of BlackCat (also known as ALPHV) ransomware-as-a-service (RaaS) operation, resulting in widespread operational disruption.
Contributing Security Gaps
Several defensive shortcomings amplified the impact of both incidents:
- Inadequate MFA enforcement, allowing attackers to bypass or manipulate authentication controls
- Insufficient employee security awareness, increasing susceptibility to social engineering
- Over-privileged identity access, enabling rapid privilege escalation once inside
- Limited identity-focused detection and response, delaying recognition of abnormal access patterns
CVE-2015-2291
CVE-2015-2291 is a local privilege escalation vulnerability in Intel Ethernet diagnostics drivers that allows a low-privileged local user to achieve kernel-level code execution through crafted IOCTL calls. While technically severe and listed in CISA’s Known Exploited Vulnerabilities Catalog, this vulnerability represents a traditional endpoint exploitation path, not the primary intrusion vector observed in Scattered Spider’s most impactful campaigns.
In contrast to the Caesars and MGM incidents, where attackers relied almost entirely on social engineering and identity abuse, CVE-2015-2291 requires prior local access and a vulnerable driver to be present. As such, it is better understood as a post-compromise enabler rather than an initial access technique, potentially used to harden persistence or escalate control on already-compromised systems.
Defending Against Scattered Spider TTPs
Scattered Spider demonstrates a fundamental shift in how modern attacks succeed. Rather than exploiting software vulnerabilities or deploying large malware payloads, the group abuses identity systems, trusted workflows, and legitimate access paths to move through environments unnoticed.
Closing Doors
Scattered Spider exploits trust in identity workflows, not software vulnerabilities. The most effective hardening measures focus on closing identity gaps at the points most frequently abused.
Lock Down Helpdesk Identity Changes
Require positive identity verification and out-of-band confirmation for high-risk changes such as password resets, MFA changes, and account recovery. Avoid reliance on static personal data.
Helpdesk Identity Change Request
→ Require real-time TOTP verification generated by the user
→ Validate TOTP before proceeding with:
- Password resets
- MFA registration or removal
- Recovery info changes
→ Block request if TOTP cannot be verifiedEnforce Phishing-Resistant Authentication
Remove SMS and voice-based MFA. Require strong, phishing-resistant MFA for all users, and stricter enforcement for privileged identities.
Restrict MFA Registration and Modification
Limit MFA changes to trusted locations and compliant devices. Investigate shared MFA devices or phone numbers across multiple accounts. For organizations that leverage Microsoft Entra ID, this can be accomplished using a Conditional Access Policy.
Reduce Standing Privilege
Enforce least-privilege access, separate admin and user identities, and use just-in-time access for privileged actions.
Bind Identity to Device Trust
Require device compliance and active endpoint protection as part of authentication. Monitor for new or unmanaged devices gaining access.
Minimize Lateral Movement Paths
Restrict remote authentication for local and service accounts and limit administrative access to hardened environments only.
Closing these doors significantly reduces the attacker’s ability to progress through the identity attack flow, shrinking the window for compromise before detection and response.
How SlashID Helps
This section outlines how an identity-first defense model disrupts Scattered Spider’s attack flow, and how SlashID detects and stops these attacks before they escalate into full-scale breaches.
Identity Visibility and Governance
Problem:
- Attackers exploit helpdesk workflows, MFA resets, OAuth grants, and dormant access
How SlashID helps:
- Unified identity graph across IdP, SaaS, cloud, and on-prem
- Shadow SaaS and GenAI access visibility
- Vishing prevention with TOTP verification
Authentication Abuse and MFA Manipulation
Problem:
- MFA fatigue, MFA re-registration
How SlashID helps:
- Behavioral detection for MFA changes and authentication method drift
- One-click or automated remediation (enforce MFA, suspend users, rotate credentials)
Privilege Escalation, Persistence and Lateral Movement
Problem:
- Over-privileged roles, OAuth abuse
- SSO-based lateral movement across SaaS
How SlashID helps:
- Detection of permission drift and risky OAuth 2.0 grants
- Identification of newly privileged users and service accounts
- Behavioral anomaly detection across the identity graph
- Shadow SaaS discovery to identify unsanctioned access expansion
Detection, Response, and Operational Speed
Problem:
- Attacks succeed because detection is delayed
How SlashID helps:
- 500+ built-in detections across your identity graph—no custom rules needed
- Native SIEM/SOAR integrations
- Connected view of users, non-human identities, and AI agents across environments
- Compliance-ready reporting (SOC 2, ISO 27001, PCI-DSS, and more)
Conclusion
Scattered Spider represents a new era of identity-centric attacks where adversaries don’t need to exploit vulnerabilities—they simply log in using stolen or manipulated credentials. Defending against these threats requires a shift from traditional perimeter security to identity-first security models that provide visibility, detection, and rapid response across the entire identity attack surface.
If you’re looking to strengthen your defenses against identity-based attacks, contact SlashID to learn how our platform can help protect your organization.


