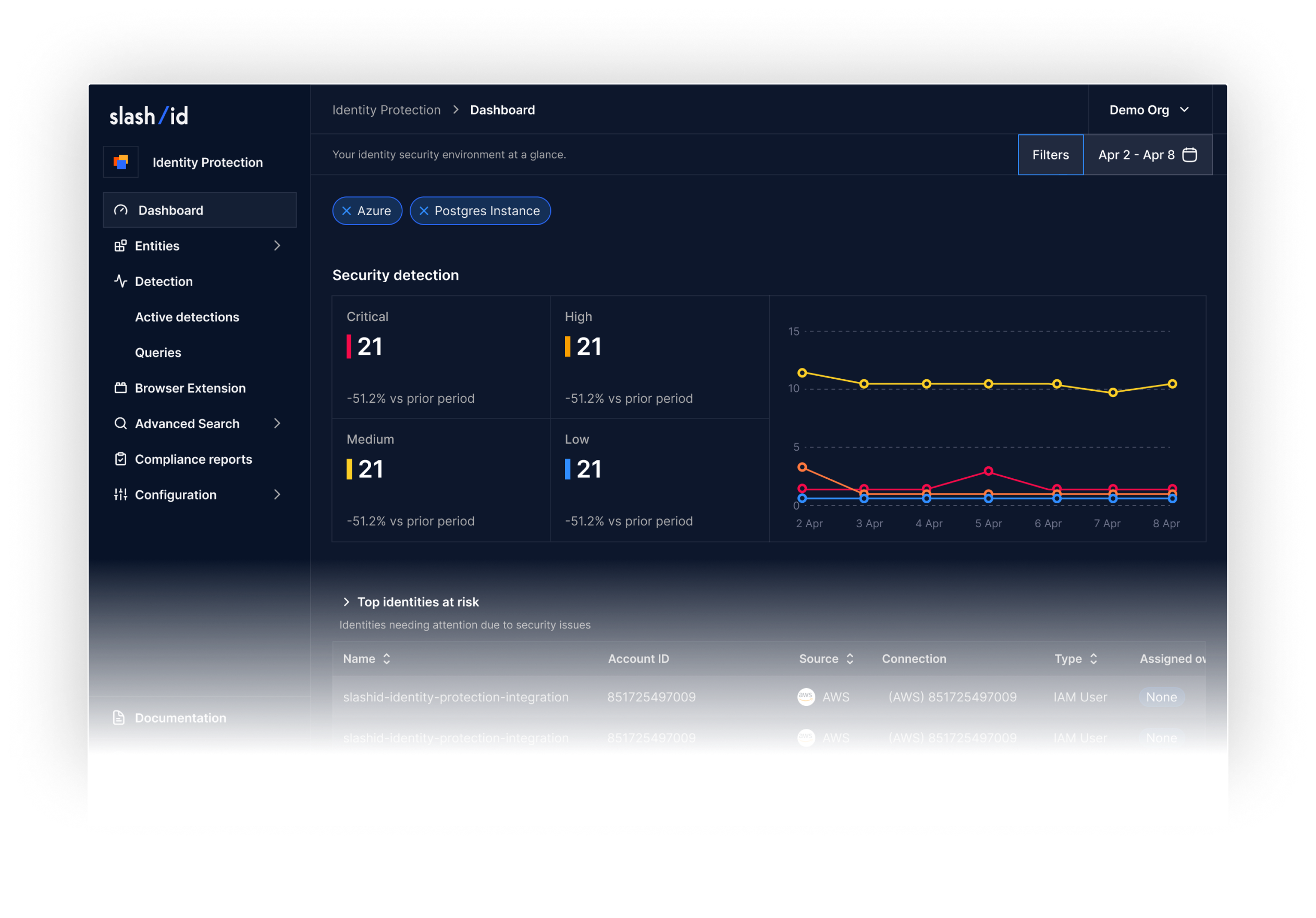
Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits. Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.